
This article explains how to configure FreeNAS to use Open Directory LDAP on OS X Server to make it easy to manage user accounts or integrate with an existing network security model.
Overview
OS X Server provides a convenient way to manage user accounts and passwords on a network with its Open Directory LDAP service. This ensures a consistent user model across multiple devices on a network.
When a file is created on one device with a specific user account, the same user can access the file from another device because thanks to the shared directory the user or group ID will match, and beyond that the user can be authenticated.
Without Open Directory, one would need to create the same account on multiple devices and ensure that passwords, user IDs, and group IDs are the same in order to setup a consistent access model.
FreeNAS can be configured to communicate with LDAP (Lightweight Directory Access Protocol) so that any access to the system can be restricted using accounts in a directory.
The high-level steps are:
- Enable Open Directory on OS X and create users and groups with Server App
- Add the LDAP service to FreeNAS
- Configure the LDAP service in FreeNAS
- Turn on the LDAP service in FreeNAS
Limitations
There are a couple things to be aware of with this configuration.
- FreeNAS does not currently configure the AFP service Netatalk to enable NFSv4 ACLs so you’re limited to POSIX semantics and will not be able to configure ACL level permissions from a remote mounted AFP share. This feature is tracked at Feature #3242 – Enable AFP ACL support when using LDAP.
- As of Lion, OS X Server no longer supports configuration as a PDC out of the box. This means Samba for CIFS sharing has to be configured in User Level Security mode and use a password database. By default FreeNAS configures itself in this mode and expects Open Directory to have been initialized with the Samba 3.6 schema and for user accounts to be initialized with password entries for Samba using something like smbldap-tools. This requires a significant amount of configuration and is covered in a separate post Configure FreeNAS Samba for OS X Server Open Directory.
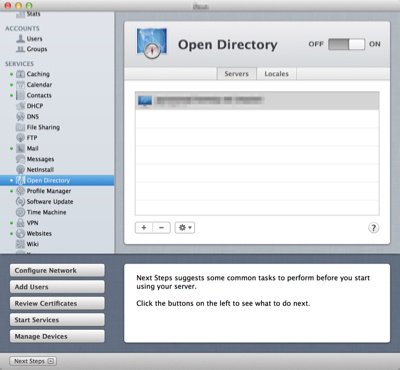
Enable Open Directory
Use the Server App to turn on Open Directory and to create user and group accounts. There are plenty of resources on the web for this and so it will not be covered here. For example, see Apple OS X Server: How to Set Up Open Directory.
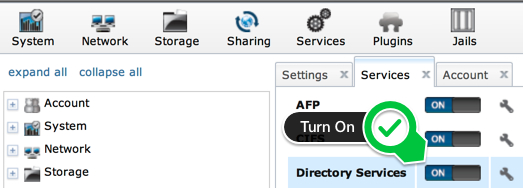
Add the LDAP Service
Directory Services will not show up in your list of services until you turn it on. Go to System / Settings and change the Directory Service to LDAP.
Configure the LDAP Service
Directory Services will now show up on the Services list and you can click the wrench to configure it.
On the configuration screen that follows you will want to set the following.
| Field | Value |
|---|---|
| Hostname | IP or yourdomain.com |
| Base DN | dc=yourdomain,dc=com |
| Allow Anonymous Binding | No |
| Root bind DN | uid=diradmin,cn=users,dc=yourdomain,dc=com |
| Root bind password | your diradmin pw |
| Password Encryption | crypt |
| User Suffix | cn=users |
| Group Suffix | cn=groups |
| Password Suffix | cn=users |
| Machine Suffix | cn=computers |
| Encryption Mode | SSL |
| Self signed certificate | OS X server contents of /etc/certificates/yourdomain.com.cert.pem, *.chain.pem |
| Auxiliary parameters | ldap_version 3 |
| timelimit 30 | |
| bind_timelimit 30 | |
| bind_policy soft | |
| pam_ldap_attribute uid | |
| sasl-host yourip.or.yourdomain.com | |
| sasl-realm YOURDOMAIN.COM |
Note the sasl-host and sasl-realm parameters which are required in order for users to be authenticated through Kerberos.
Turn on the LDAP Service
You can now click the toggle on the Services tab to enable Directory Services.
Verify LDAP Connectivity
Use the Shell to see whether your LDAP groups are listed.
# getent group
...
network:*:69
audit:*:77
www:*:80
yourgroup:*:1025:youruser1,youruser2
Towards the bottom you should see a list of groups from your directory. You can also check getent passwd for a list of users.
You may wish to review /var/log/messages for any errors.


After reading this good article I’m considering testing FreeNAS for Apple network home directories either AFP or NFS.